When logging into computer systems, using email, or accessing various social networking sites, the first step typically involves entering a username and password. If authentication credentials are compromised, they can be exploited. Dr. Albert Guan, Assistant Professor in the Department of Computer Science and Information Engineering at National Taiwan Normal University, has pioneered research on “A Novel Verification Scheme to Resist Online Password Guessing Attacks.” This research has effectively tackled the risks related to passwords, offering innovative insights into information security.
In modern information systems, usernames and passwords are the most commonly used mechanisms for verifying user identities. Although the public generally understands the importance of protecting their accounts and passwords, incidents of account misuse remain frequent. The primary reason is that poorly conceived password settings can be easily guessed, which, like the leakage of account credentials, can lead to identity theft. This type of threat is referred to as a "password guessing attack."
To prevent passwords from being guessed, Dr Albert Guan explains that a common authentication method is to limit the number of password attempts for the same account to a maximum of three within a certain time frame. If all three attempts fail, further attempts are blocked, and users must wait before trying again. However, this approach addresses only the symptom but not the underlying issue. Another method requires passwords to have a certain length and complexity criteria. While this makes passwords harder to guess, they are also harder for users to remember, reducing convenience.
In response to these challenges, Dr Albert Guan launched research aimed at finding a simple yet effective method to prevent malicious password guessing attacks and account theft. His research begins by analysing the behaviour patterns of users when they enter their usernames and passwords, aiming to distinguish legitimate users from attackers. The study assumes that the legitimate user knows their password, while the attacker has no prior knowledge of the password and can only make guesses. Using probability and statistics, Dr Guan developed a mathematical model to represent the behaviours of both users and attackers. He then applied principles from information theory to determine whether an entered password is likely to come from the user or an attacker.
For example, let's examine the following two different password-entering scenarios:
A: admin, wellcome, welcome
B: abc123, password, welcome
Dr Guan explains that even though both scenarios involve successfully entering the correct password on the third attempt, most people would consider User A as a legitimate user and User B as a possible attacker. The reasoning lies in the behaviour: User A might have accidentally entered the password for a different account on the first attempt, typed an extra character on the second attempt, and then succeeded on the third. In contrast, User B’s attempts seem more like intentional trial and error. This observation inspired the research team to establish a theoretical framework to support such judgments.
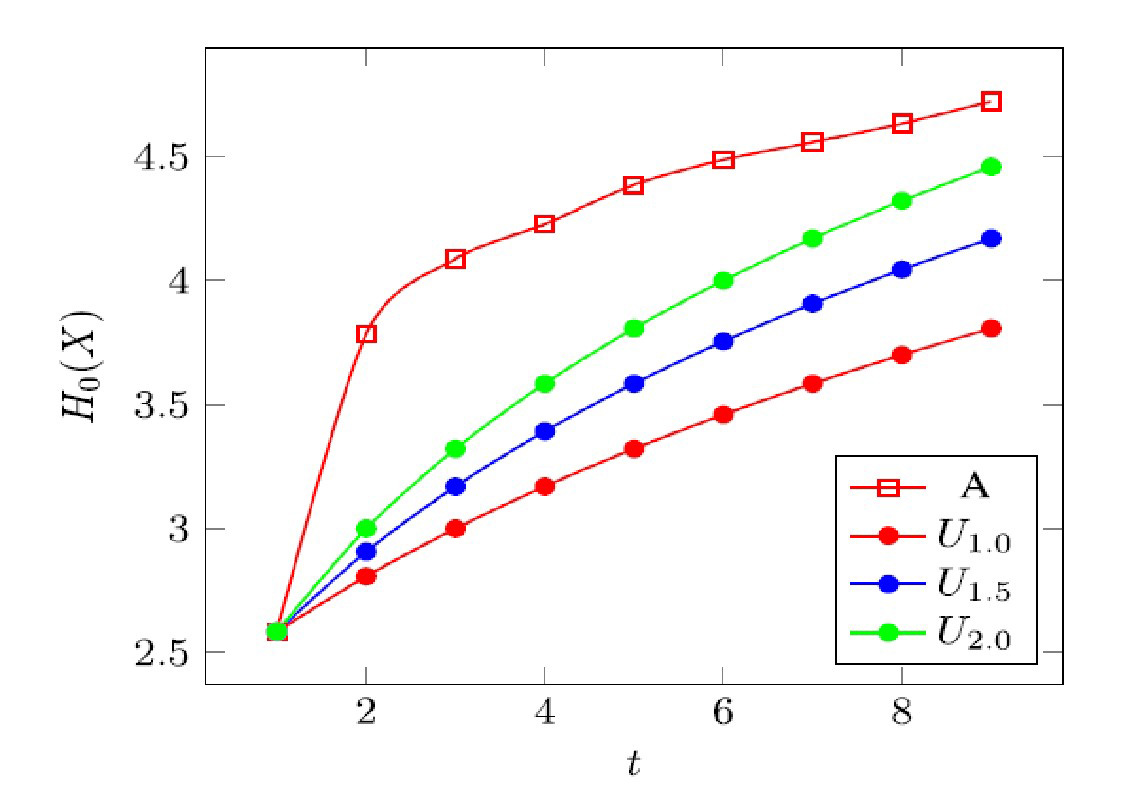
Figure 1: Entropy values of different password strings calculated by the research team
Based on the research results shown in the above graphs, Dr Guan analysed that the dark red line represents the entropy of password strings entered by attackers, while the other three lines in different colours represent the entropy of password strings entered by legitimate users. The graph reveals that even if users make an average of two typing errors per password attempt, the entropy of their input remains lower than that of random guesses made by attackers. This disparity is particularly pronounced when it takes 2 to 4 attempts for the user or the attacker to enter the correct password. This finding indirectly validates the rationale behind the commonly used authentication mechanism of blocking further password attempts after three consecutive failures.
The research team employed the concept of uncertainty to develop their inference method and ultimately designed a simple yet effective approach to estimate whether a password input is the result of "random guessing." The method involves calculating the number of unique characters used in the entered password strings. For example, if User A's input contained 12 unique characters while User B's input included 18 unique characters, it can be inferred that A is likely a legitimate user, whereas B is more likely an attacker.
Dr Guan explains that this new authentication mechanism is not only theoretically valuable but also highly practical. It requires only minor modifications to existing user authentication systems and does not rely on knowing the user's original password. This makes it easy to integrate into current authentication systems. The mechanism improves password security by allowing users to choose easily memorable passwords while simultaneously preventing password guessing attacks.
It is important to note that this research does not diminish the value of strong passwords. Strong passwords are inherently challenging to guess and remain essential. The primary contribution of this study is its ability to provide an added layer of protection to existing password systems, regardless of the strength of the chosen password. When suspicion arises, the system can activate a secondary authentication process to enhance security further.
Regarding future advanced research, Dr Albert Guan stated that, in addition to collaborating with industry to enhance the applicability of the study, further research could focus on estimating the residual uncertainty of passwords after multiple failed guessing attempts by attackers. When the uncertainty drops below a certain threshold, the system could notify users to change their passwords, thereby reducing the risk of account compromise. (This article was provided by The Center of Public Affairs.)
Source:
Guan, A., & Chen, C. M. (2022). A novel verification scheme to resist online password guessing attacks. IEEE Transactions on Dependable and Secure Computing, 19(6), 4285-4293.https://ieeexplore.ieee.org/document/9773951



